Windows Security, Maintenance and Optimizing Guide based on applications - in 9 Easy Steps + More! (by AXS (XSAlliN))
[1] - Antivirus & Firewall
After a fresh Install and all the necessary Updates the next step is an Antivirus and a Firewall:NOD32 + Outpost Firewall PRO is a good combination from the commercial class, let's not forget Kaspersky Anti-Virus but you can also find free alternatives that are pretty good like: Avira AntiVir PersonalEdition Classic & AVG Free Edition as antivirus and Comodo Firewall & Agnitum Outpost Firewall Free as firewall.
==================================================
[2] - Anti Spyware,Adware, & Trojans
That's good for the main security, now let's move on to the next step, AntiSpyware,Adware, & Trojans security, from the comercial class one of the best is Spy Sweeper, but it's good to have more then one protection since there are no conflicts at this category so let's move on to the free applications like Ad-Aware SE Personal, Spybot - Search & Destroy, AVG Anti-Spyware (Free Scaner/Remover - Trial Active Shield)
Spyware Blaster /Spyware Guard both made by Javacool - One passive, one active.
Other good tools which got good enough by 2008 to worth mentioning:
Malwarebytes (recommended by SparkyJJO) - It has am active support forum so this tool is properly verified, tested and updated by it's owner.
SUPERAntiSpyware - The name might look tricky, at first I fought is was a rogue, so I verified it and it turned up to be legit, tested it and prove to be quite efficient.
HijackThis - and advanced detection tool made by a guy named Merijn, which now belongs to TrendSecure. I didn't post before, yet I knew about it cause it could be dangerous if used by a beginner. On the other hand, even a beginner could copy the advanced report and paste it on a forum for analysis by advanced users. Was recommended by SnakeEyez before and now it has my recommendation, cause it could be useful for finding unknown threats - but use it with caution cause this is not a simple Scan and Fix tool.
WARNING! the internet it's full of fake software even from the commercial class, you should check rogue anti-spyware for more information about this fake products and other PC Security related stuff
In the end I'd like to add an Excellent advice, posted by Lorna Hutcheson:
Tools are simply that...just tools. As you work with malware, its important to have many ways to confirm your results. Its just as important NOT to totally rely on your tools to provide you with the answers. You HAVE to understand the tools your using. Don't become so dependent on one way of verifying something. I run many tools at the same time when I work with malware. Each has a different purpose as well as strengths and weaknesses. It's important to know them and not just rely on a single method. In essence you want to look at malware from many different angles and never forget that your tools are only so good and may not provide you with the right answer. Nothing can replace your analysis skills and your ability to understand what your seeing.
==================================================
[3] - Anti-Rootkits
You need a specific definition to detect this whit an Antivirus or Antispyware application, some rootkits can be detected whit a process explorer (Like those at Nr.5 - from this Guide) - here is a good tool similar to those:
IceSword
Try this link for Anti-Rootkit Software - Detection, Removal & Protection, plus more, like the latest News on Rootkits, a Rootkit List and other stuff good to know about this threat.IceSword is an effective tool against "rootkits," virus-type programs that can evade detection by ordinary antivirus products.
IceSword has a Windows Explorer-like interface but displays hidden processes and resources that Windows Explorer would never show. It isn't a "click-here-to-delete-rootkits" product but a sophisticated discovery tool that can protect against sinister rootkits if used before they infect a machine.
Definition:NOTE: As you can see in the definition above, rootkits can be found on a variety of operating systems, I personally found more on some clients servers (Linux based), but friends found those in Windows OS - I recommend you scan both "PC and Server" just to be sure.A root kit is a set of tools used by an intruder after cracking a computer system. These tools can help the attacker maintain his or her access to the system and use it for malicious purposes. Root kits exist for a variety of operating systems such as Linux, Solaris, and versions of Microsoft Windows.
==================================================
[4] - Windows Services
Assuming that you changed IE 6.0 with a secure Browser like Firefox or Opera we should move to the next step: Windows Services, I found a good link at TechSpot with all the services explained plus other informations, it's good to now what to disable this could increase your system performance.
WARNING! Do NOT use "msconfig" to disable services, type "services.msc" in the Run box instead!
The reason is because with msconfig and Hardware Profiles, you can disable services that may be vital to boot your system. With the management console (services.msc) you cannot. Also, msconfig, while unchecking the box, is disabling the service.
The "Disable All" button also scares me. It should not even be there as no reason exists to justify disabling "everything." (a good advice originaly by BlackViper)
==================================================
[5] - Startup Files & Process Explorer
After installing all your everyday applications you should check the "Startup List" so you know what starts whit you Windows OS, by stooping some of them that you don't need or don't use only occasionally could speedup windows boot and general performance, I personally recommend using "Quick Launch Bar" for quick access to some applications, NOT System Try - use S.T. only for active application like AV and Firewall, you could use the next application for this purpose (to see what starts whit Windows):
Autoruns
Another useful tool is Unlocker, this could help you "DELETE" files that can't be deleted whit in the normal way. (I'm not talking about Windows Files - stay out of that placeThis utility, which has the most comprehensive knowledge of auto-starting locations of any startup monitor, shows you what programs are configured to run during system bootup or login, and shows you the entries in the order Windows processes them. These programs include ones in your startup folder, Run, RunOnce, and other Registry keys. You can configure Autoruns to show other locations, including Explorer shell extensions, toolbars, browser helper objects, Winlogon notifications, auto-start services, and much more. Autoruns goes way beyond the MSConfig utility bundled with Windows Me and XP.
Autoruns' Hide Signed Microsoft Entries option helps you to zoom in on third-party auto-starting images that have been added to your system and it has support for looking at the auto-starting images configured for other accounts configured on a system. Also included in the download package is a command-line equivalent that can output in CSV format, Autorunsc)
For a quick shutdown the solution is simple just install User Profile Hive Cleanup Service. If that doesn't work, simply remove manually all the applications from your system try.Ever had such an annoying message given by Windows?
It has many other flavors:
Cannot delete file: Access is denied
There has been a sharing violation.
The source or destination file may be in use.
The file is in use by another program or user.
Make sure the disk is not full or write-protected and that the file is not currently in use.
Unlocker is the solution!
1. Simply right click the folder or file and select Unlocker
Now it's time to look at your WinTasks Process Library, sometimes here you can find some uninvited guests, here are some applications that could help you with this (Atutoruns is good even for this):
Process Explorer
The Process Explorer display consists of two sub-windows. The top window always shows a list of the currently active processes, including the names of their owning accounts, whereas the information displayed in the bottom window depends on the mode that Process Explorer is in: if it is in handle mode you'll see the handles that the process selected in the top window has opened; if Process Explorer is in DLL mode you'll see the DLLs and memory-mapped files that the process has loaded. Process Explorer also has a powerful search capability that will quickly show you which processes have particular handles opened or DLLs loaded.
The unique capabilities of Process Explorer make it useful for tracking down DLL-version problems or handle leaks, and provide insight into the way Windows and applications work.
Process Explorer works on Windows 9x/Me, Windows NT 4.0, Windows 2000, Windows XP, Server 2003, and 64-bit versions of Windows for x64 processors, and Windows Vista.
EzPcFix
==================================================Ez-Pc-Fix is very helpful when trying to remove viruses, spyware and other troublesome advertising programs and malware from your computer because it shows you what's being started on your system and where it's getting started from (and it let's you remove them).
[6] - Registry Tweaks
Next in line are the Registry tweaks but it's real boring to make all the changes from "regedit" since there are some applications that could help out with this request:
xp-AntiSpy ( quick windows settings tweaker for XP or Vista )
xpy (quick windows settings tweaker)The xp-AntiSpy is a little utility that lets you disable some built-in update and authentication 'features' in WindowsXP.
For example, there's a service running in the background which is called 'Automatic Updates'. I don't know what this service transfers from my machine to other machines on the internet, especially the MS ones. So I play it safe and disable such functions. If you like, you can even disable these functions manually, by going through the System and checking or unchecking some checkboxes. This will take you approximately half an hour. But why wast time when a little neat utility can do the same in 1 minute?
Small tool which disables the default threats of a Windows XP installation. Besides disabling Windows and some of its components to communicate with Microsoft servers, xpy improves privacy settings and your system’s security.
Features:
• Disable Windows “calling home”
• Disable questionable services
• Disarm Internet Explorer
• Disarm Windows Media Player
• Remove Windows Messenger
• Improve privacy and security
• Improve performance
Though xpy is smaller than 60 kilobytes, it can close serious threats (i.e. DCOM) on long distance, where large service-packs can only protect you until a new security hole has been found.
SG TCP Optimizer (Network/Internet connection Tweaker)This radical, new tool is the one of the best and most powerful Windows XP tweakers ever, supporting totally unseen tweaks, which is unique to the program.
Features:
· Ultra-fast boot (rearrange boot files)
· Boot folder defragmentation
· Prefetch folder cleaning
· DNS cache optimization
· File allocation size tweak
Windows Half-open limit fix (patch) (Works even with Vista 64 bit SP1 and you don't have to disable digital driver signing)Description: The TCP Optimizer is a free, easy Windows program that provides an intuitive interface for tuning and optimizing your Internet connection. There is no installation required, just download and run.
The program can aid both the novice and the advanced user in tweaking related TCP/IP parameters in the Windows Registry, making it easy to tune your system to the type of Internet connection used. The tool uses advanced algorithms, and the bandwidth*delay product to find the best TCP Window for your specific connection speed. It provides for easy tunning of all related TCP/IP parameters, such as MTU, RWIN, and even advanced ones like QoS and ToS/Diffserv prioritization. The program works with all current versions of Windows, and includes additional tools, such as testing average latency over multiple hosts, and finding the largest possible packet size (MTU).
Default Value: 10 connections
------------------------------------Program Half-open limit fix intend for changing maximum number of concurrent half-open outbound TCP connections (connection attempts) in system file tcpip.sys.
This limit is entered by company Microsoft trying to make slower virus spreading from infect computer and cut down opportunities of participation of a computer in DoS attacks.
First this limit was entered in SP2 for Windows XP and present at all new versions of Windows. Limit consists that the computer is not authorized to have more than 10 concurrent half-open outbound connections. At achievement of a limit new attempts of connections are put in turn.
Thus, speed of connection to other computers is actually limited.
This limit is especially critical for P2P programs (µTorrent, BitComet, eMule, P2PTV etc.) users. When the P2P program works, pages in a browser can be loaded extremely slowly. The delay before the beginning of opening can make some tens seconds irrespective of speed of your connection.
Half-open limit fix cleans this limit, that is increases the maximal limit of half-open connections. For the overwhelming majority of users there will be sufficient a limit equal 100.
For cleaning you could use CCleaner (Cleaner, Software uninstaller and Startup Manager):
and
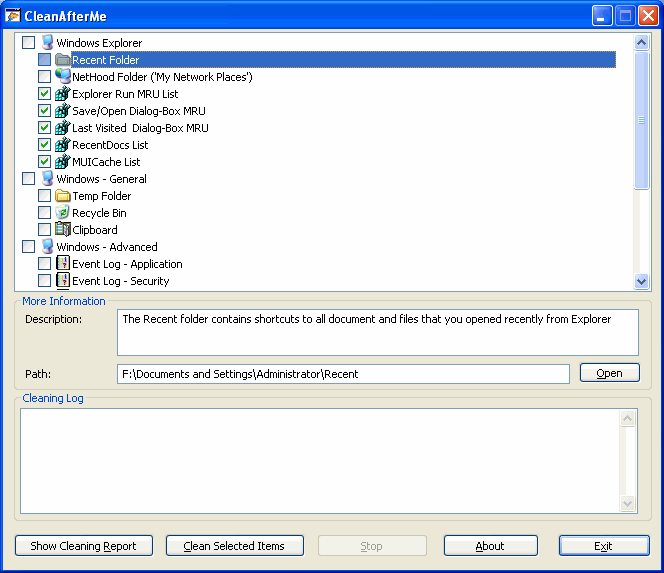
CleanAfterMe
The myth about Registry Cleaning was busted and yeah, it's true you won't see a big improvement after using those cleaners but they're good for general cleaning (like recently used files which or temporary stored in different folders even registry values).
WARNING: It's good to add that some Registry Cleaners or dangerous, since they try to clean what they shouldn't and that could make you OS unstable. With XP most of them were harmless but with Vista even those could be dangerous.
"WinXSX" is one of the causes behind this danger. That directory is a massive library of .dll files which they constantly update whith every new application installed (that why it grows in size) for compatibility purpose. Some registry cleaners aren't capable of understating that and they delete the registry value of old or recently installed .dll files. That could lead to applications incompatibility or SO instability.
==================================================
[7] - HDD Maintenance
All deleted files leave some traces behind, which in time feel like a burden for you HDD. Fortunately tools like Eraser can clean those junk files. Even cover traces of your sensitive data, files that you deleted and don't want to be recovered. In case you sale you HDD, or change your work place and feel like leaving a clean desk - for example.
Copying/Deleting/Installing/Downloading - basically all intensive actions that interact with your HDD lead to one thing: Fragmented files - You all have some favorite tool for defragmenting your HDD, even the one included in Windows. Most of them or classic tools, or should I say "Old tools" with a modern interface. I personally am against this tools that require a lot of time to do their work and all that time they stress your HDD to maximum. I even consider them dangerous, but since I have no prof I'll let you decide what's best for your HDD.Eraser is an advanced security tool (for Windows), which allows you to completely remove sensitive data from your hard drive by overwriting it several times with carefully selected patterns. Works with Windows 95, 98, ME, NT, 2000, XP, Windows 2003 Server and DOS.
Eraser is Free software and its source code is released under GNU General Public License.
The patterns used for overwriting are based on Peter Gutmann's paper "Secure Deletion of Data from Magnetic and Solid-State Memory" and they are selected to effectively remove magnetic remnants from the hard drive.
Other methods include the one defined in the National Industrial Security Program Operating Manual of the US Department of Defense (DoD 5220.22) and overwriting with pseudo random data. You can also define your own overwriting methods.
I found this "Defragmenting Tools Roundup" which might help you understand the benefits of defragmenting, it might even help you choose the right tool for your needs. I personally found Eraser combined with JkDefrag to be the best solution. I use Eraser to Erase Unused Space which clears all the junk from previously deleted files, fallowed by JkDefrag which covers the disk defragmentation and optimization needs. After this treatment, your HDD will act just like a new, freshly formatted HDD.
The next tools are great for HDD statistics, like: Health (based on SMART), partition size, etc. I also recommend using the main tools from your HDD manufacture, like: Data Lifeguard Tools from "Western Digital".
Now the good stuff, at first I'd like to recommend WinDirStat wich is a disk usage statistics viewer and cleanup tool for Microsoft Windows (all current variants). - found this great tool accidentally, originally was recommended by nn_step for another user, plus it's free.
Another great tool could be HDD Tune, a Hard Disk utility which has the following functions:
It's good for his purpose and it's also free.* Benchmark: measures the performance
* Info: shows detailed information
* Health: checks the health status by using SMART
* Error Scan: scans the surface for errors
* Temperature display
==================================================
[8] - Backup Tools
Now that all is clean and fresh you should make a BackUp so you could prevent future problems, you could use Paragon Drive Backup , Acronis True Image or Cobian Backup (this one is Free).
==================================================
[9] - Boot Management Tools
Let's not forget some vital tools for critical times (like not being able to install the OS because of blue screens and other problems that might occur in this stage), an all in one package whit lots of great stuf for management,Testing, Diagnosis and more - you don't need no OS for this just create a Boot CD/DVD/USB set your system (BIOS) to Boot from this devices and you're On, so here they are:
Ultimate Boot CD
Or you could try something more complete in some ways and more famous for it's stuff: Hiren's BootCD it has most of the things from the one above plus more.Ultimate Boot CD
The basic version contains updated versions of all tools found in previous releases and even adds a few more. This version does not contain the Linux boot environment INSERT.
Hard Disk Installation
MaxBlast (Maxtor)
DiscWizard (Seagate)
Disk Manager (Seagate)
Disk Manager (Samsung)
Hard Disk Diagnosis
Drive Fitness Test (IBM/Hitachi)
PowerMax (Maxtor/Quantum)
SCSIMax (Maxtor)
DLG Diagnostic (Western Digital)
Data Lifeguard (Western Digital)
SeaTools Desktop (Seagate)
Diagnostic Tool (Fujitsu)
SHDIAG (Samsung)
HUTIL (Samsung)
GWSCAN (Gateway)
GWSCAN (Gateway)
Salvation HDD Scan and Repair
MHDD32
ExcelStor's ESTest
Hard Disk Device Management
Feature Tool (IBM/Hitachi)
AMSET (Maxtor)
MAXLLF (Maxtor)
UATA100 (Seagate)
Ultra ATA Manager (Western Digital)
SMARTUDM
ATA Password Tool
ATAINF
ExcelStor's SATA Tool
Hard Disk Wiping
AutoClave (Discontinued)
Active@ KillDisk Free Edition
Darik's Boot and Nuke
PC INSPECTOR e-maxx
Hard Disk Cloning
HDClone (Free Edition)
g4u
PC INSPECTOR clone maxx
XXCOPY
Hard Disk Sector Editor
Disk Editor
DISKMAN4
PTS DiskEditor
Partition Tools
Ranish Partition Manager
XFDISK (Extended FDISK)
SPFDISK (Special FDISK)
TestDisk
Partition Resizer
Partition Saving
Free FDISK
MBRtool
MBRWork
FIPS
Active@ Partition Recovery
Boot Managers
Smart BootManager
Gujin
GAG
XOSL
Super Grub Disk
File Tools
DOS Navigator
File Maven
Necromancer's DOS Navigator
Eraser for DOS
D-Browse
NTFS Tools
Offline NT Password & Registry Editor
Active NTFS Reader for DOS
EditBINI
Boot Partition
NTFS4DOS n/a
System Burn-In Test
Lucifer
CPU Test
CPU Burn-in
Mersenne Prime Test
StressCPU
Memory Test
Memtest86
Memtest86+
Windows Memory Diagnostic n/a
DocMem RAM Diagnostic
DocMem RAM Diagnostic
TestMem4
Peripherals Test
Parallel port detection and test utilities
ATAPI CDROM Identification
CHZ Monitor-Test
CPU Information
Intel Processor Frequency ID Utility
x86test
System Information
AIDA16 (Discontinued)
PC-Config 9.33
NSSI
ASTRA
PCISniffer
PCI
CTIA
Benchmark Applications
System Speed Test
3D Benchmark VGA
CPU Benchmark
CD Index
QwikTest
BIOS Utilities
BIOS
WipeCMOS
CMOSPWD
!BIOS
DOS Boot Disks
FreeDOS Boot Disk
OpenDOS Boot Disk
NwDsk: NetWare Boot Disk
MSRRC: Bart's Network Boot Disk on FreeDOS
Antivirus Tools
F-Prot Antivirus for DOS (Personal use only)
McAfee Antivirus Scanner
Avast! V7.7 for DOS
AVG Free Edition
Network Tools
Freesco
Note: First you need to create a configuration floppy disk based on freesco/freesco.zip on the CD
Arachne WWW Browser
QNX Demo Browser (network and modem version)
NetCopy
DOSRDP
FileLink
DOS Boot Disks
LZ-DOS Boot Disk
FreeDOS Boot Disk
OpenDOS Boot Disk
MS-DOS Boot Disk
NwDsk: NetWare Boot Disk
MSRRC: Bart's Network Disk Clone
Linux Boot Disks
Tom's Boot Disk
BasicLinux
Trinux
==================================================
Security Analyzer/Advisor - I'm sure there are a lot of guides and tools for this porpuse so I'll give you two of them - the most advanced in my opinion Belarc Advisor - Free Personal PC Audit and Microsoft Baseline Security Analyzer.
Hope you could have a better experience in Windows whit this personal Basic/Advanced guide, 8 Steps (+ the additional Security Analyzer/Adviser) for a better security, Performance and a Cleaner and more stable System







 Reply With Quote
Reply With Quote

Bookmarks